
MongoBleed (CVE-2025-14847): When MongoDB Compression Leaks Memory
Introduction: “Heartbleed vibes,” but for MongoDB
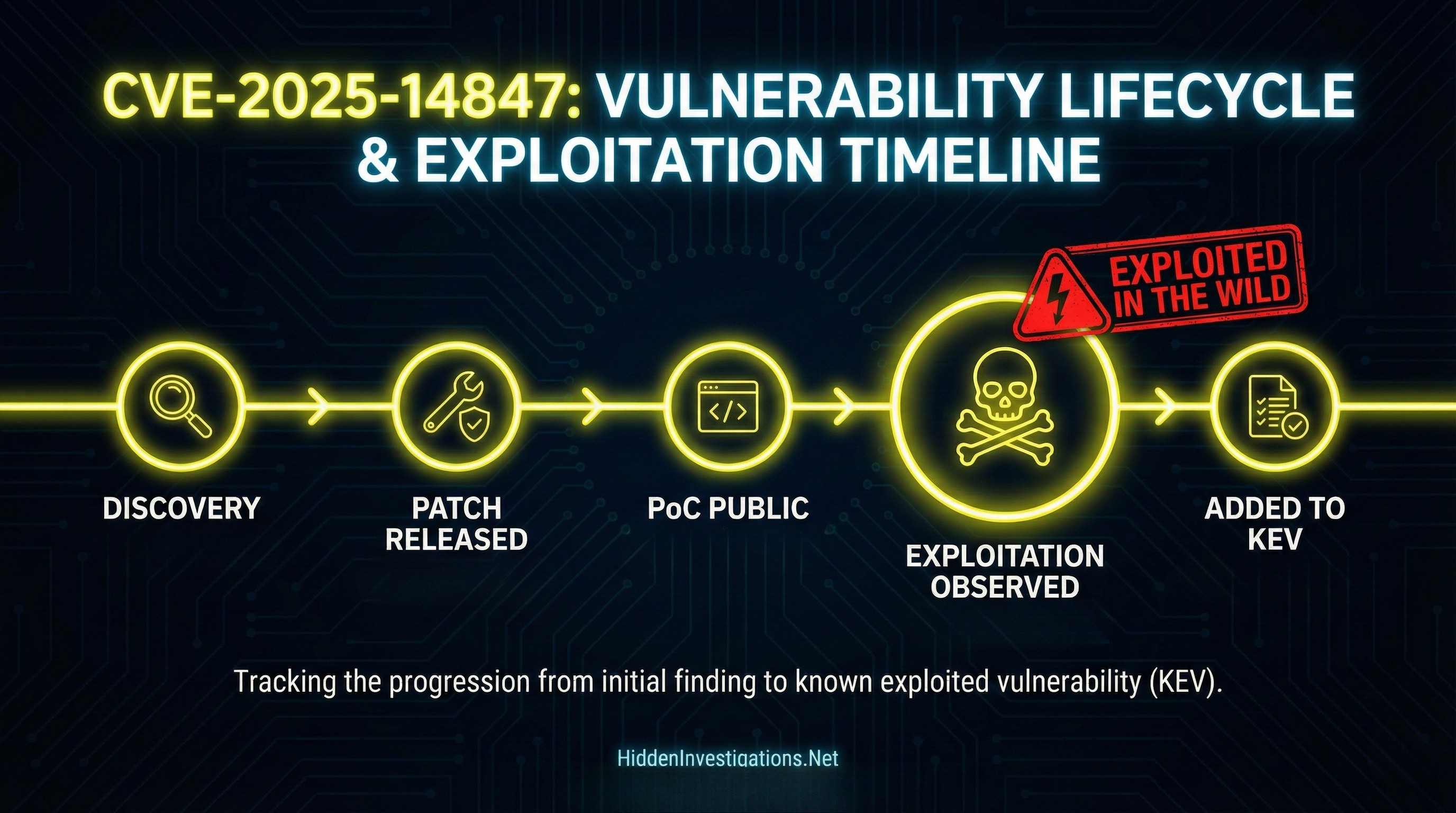
In late 2025, researchers disclosed MongoBleed (CVE-2025-14847), a vulnerability that feels uncomfortably familiar: a length mismatch leads to a memory over-read, and sensitive fragments can “bleed” out of process memory without needing valid credentials.
While MongoBleed is “only” an information disclosure bug (not direct RCE), modern environments make that distinction blurry: leaking just one admin credential or cloud token can be enough to pivot into full compromise.
What is MongoBleed, exactly?
MongoBleed is a flaw in MongoDB Server’s wire protocol decompression path when handling zlib-compressed messages. At a high level:
A client message includes a field that declares the expected uncompressed size.
The server allocates a buffer based on that declared size.
If the decompressed content is actually smaller, part of the buffer remains uninitialized.
Due to incorrect size handling, the server may return more bytes than were actually written, causing a leak of “dirty” heap memory.
Why that matters: heap memory can hold all the things you never want to leak SCRAM auth materials, DB connection strings, API keys, cloud credentials, JWTs, and even fragments of documents in flight.
Why defenders should treat this as “high urgency”
1) It’s pre-auth and network reachable
MongoBleed can be triggered before authentication, meaning any reachable MongoDB server is a potential target.
2) Exploited in the wild + KEV pressure
This vulnerability has been reported as actively exploited, and NVD’s record indicates it was added to CISA’s Known Exploited Vulnerabilities list (with a federal remediation due date).
3) Exposure scale is real
Researchers observed large numbers of exposed MongoDB services and highlighted the risk of opportunistic scanning against internet-reachable databases.
Affected versions (and the patched targets)
The affected range is broad across multiple major series, with patched releases published by MongoDB.
Patch baselines (upgrade to these or newer):
| Version | Vulnerable Range | Fixed Version | Status |
| 8.2.x | 8.2.0 – 8.2.2 | 8.2.3 | ✅ Patched |
| 8.0.x | 8.0.0 – 8.0.16 | 8.0.17 | ✅ Patched |
| 7.0.x | 7.0.0 – 7.0.27 | 7.0.28 | ✅ Patched |
| 6.0.x | 6.0.0 – 6.0.26 | 6.0.27 | ✅ Patched |
| 5.0.x | 5.0.0 – 5.0.31 | 5.0.32 | ✅ Patched |
| 4.4.x | 4.4.0 – 4.4.29 | 4.4.30 | ✅ Patched |
Legacy/EOL note: 4.2 / 4.0 / 3.6 are listed as end-of-life with no official patches, so you must mitigate (especially by disabling zlib compression + restricting access) and plan an upgrade.
MongoDB also states that Atlas and other managed offerings were updated/mitigated on their side during response actions.
How the “bleed” works (visual-first explanation)
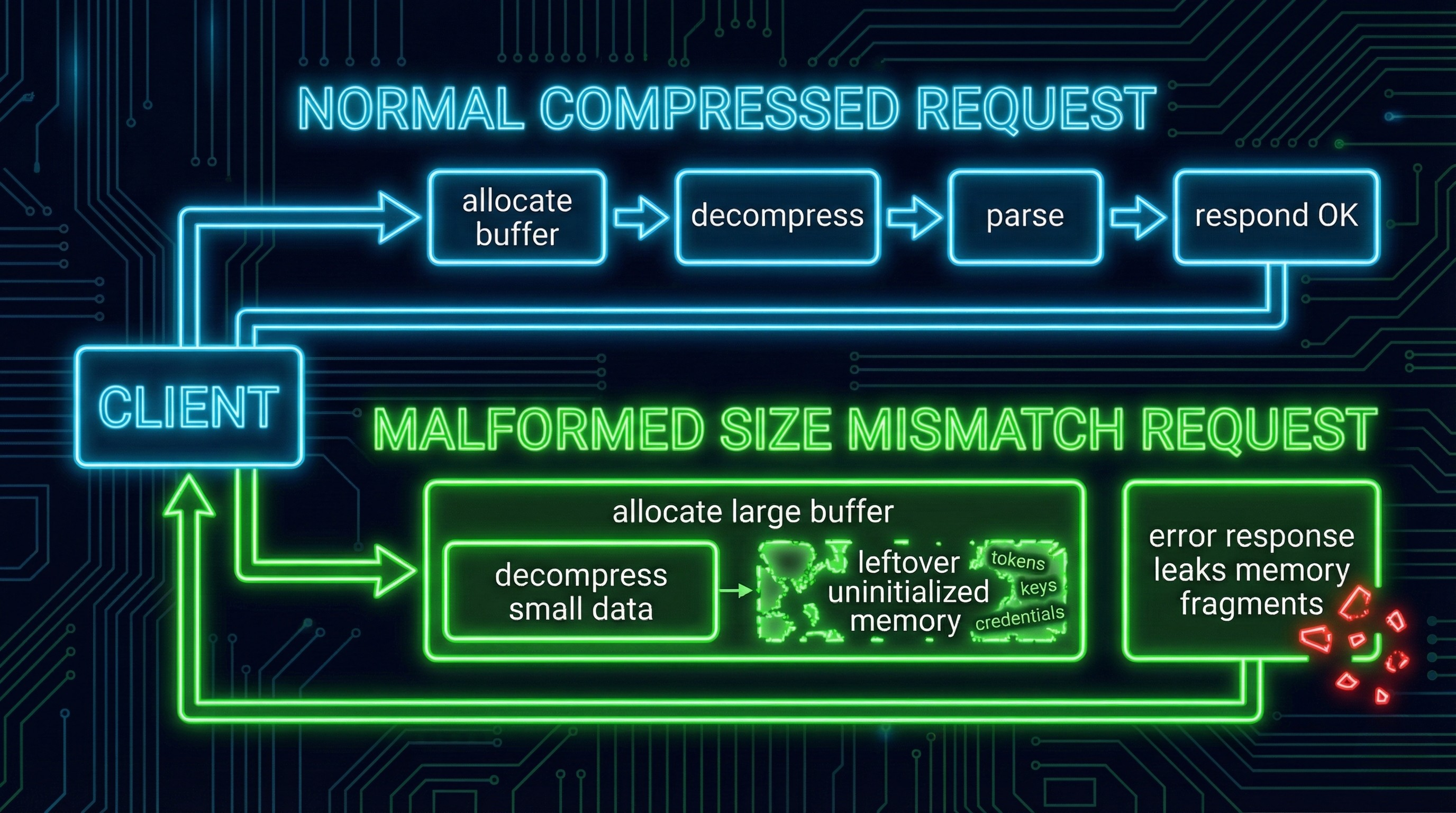
Think of it like this:
The attacker convinces the server to prepare a big box (buffer).
The attacker only puts a tiny object in the box (small decompressed payload).
The server mistakenly ships the entire box back including whatever random stuff was already inside.
The important ingredients (defender view)
Compression is involved (zlib path).
Length fields matter.
The leak is heap memory (uninitialized/previously used data).
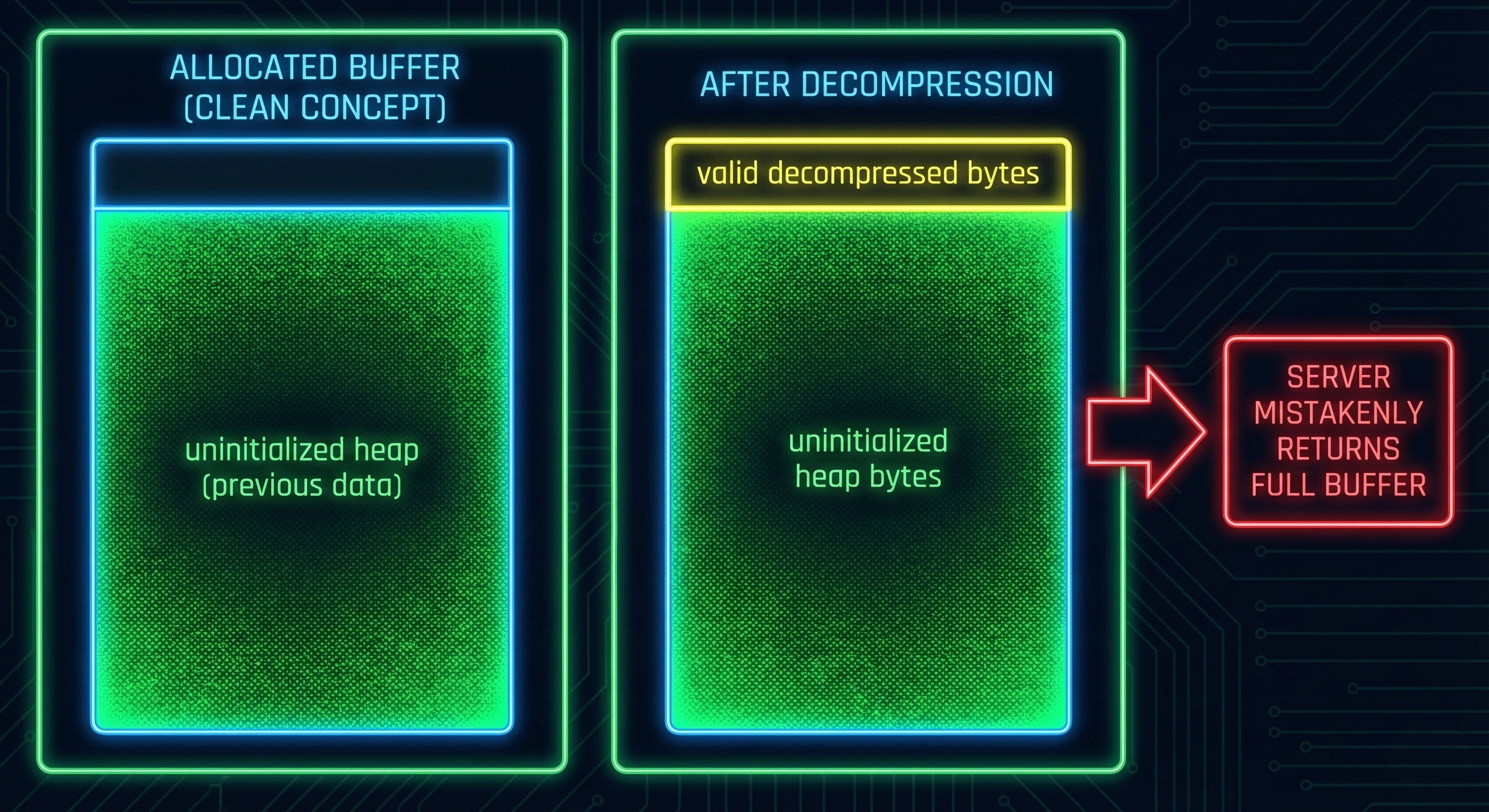
Real-world risk: what can leak?
From research writeups, leaked memory may contain:
Authentication material (e.g., SCRAM-related data)
Cleartext secrets (API keys, tokens, connection strings)
Cloud credentials in environment/config contexts
Fragments of documents/PII processed by the server
This is why incident response guidance generally treats memory disclosure like a potential credential compromise, not a simple “patch and move on.”
Detection & hunting ideas (practical)
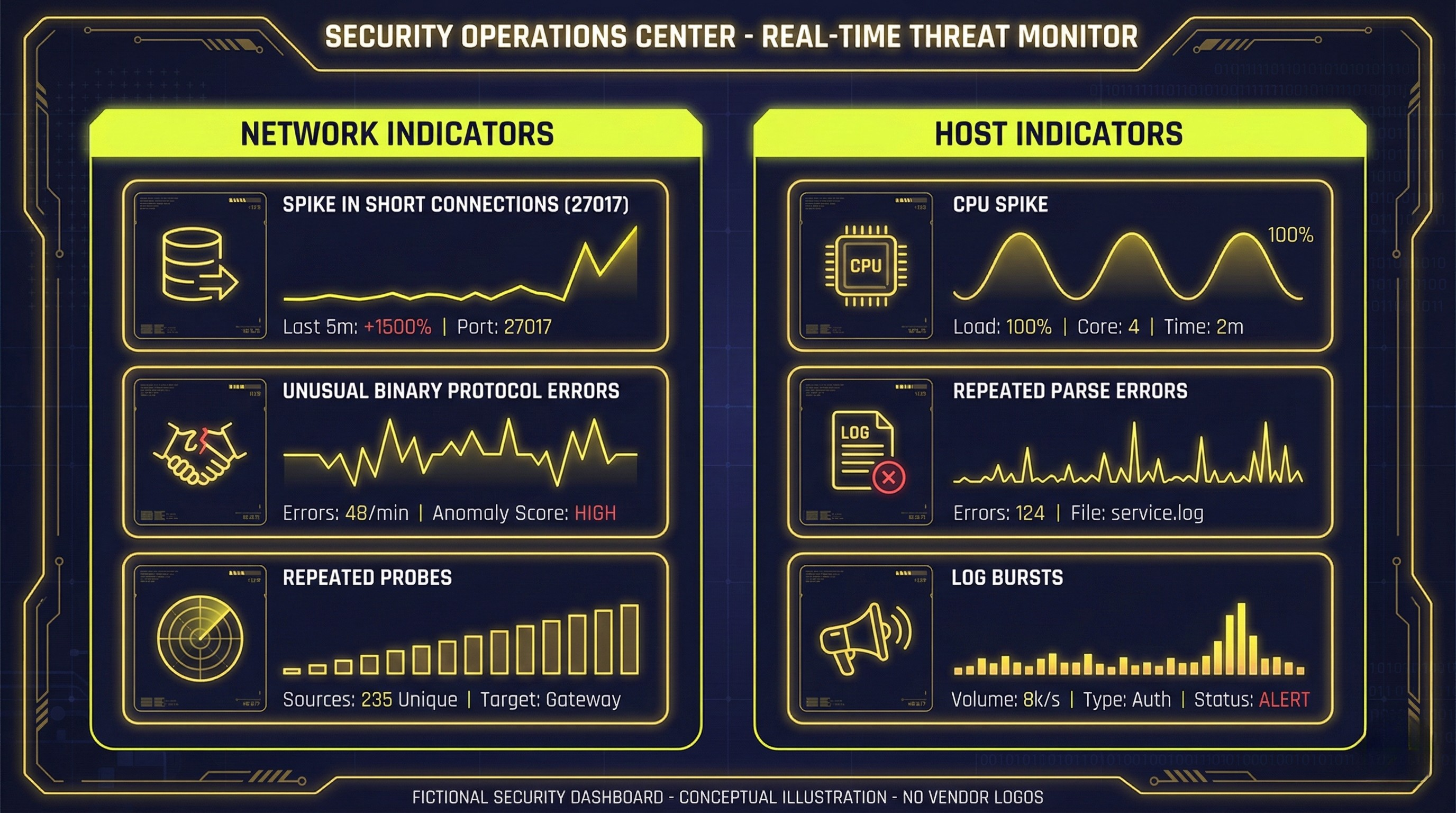
Network-side signals (what to look for)
Sudden spikes of short-lived connections to MongoDB (27017) from unfamiliar IPs
Lots of parsing/invalid-message behavior (binary protocol misuse)
Repeated attempts that don’t resemble a normal driver handshake pattern
Phoenix and Wiz both emphasize that exploit traffic tends to look unlike normal app-driver traffic and may appear as high-volume, repetitive probing.
Host-side signals
MongoDB process resource spikes with little “real” workload
Bursts of errors indicating malformed/invalid messages (if you log at sufficient verbosity)
Remediation playbook (do this in order)

1) Contain exposure (NOW)
Block public access to MongoDB (27017). Allow only app subnets / VPN / bastion.
Confirm from an external vantage point that the port is no longer reachable.
2) Patch to fixed versions (same-day)
Upgrade to the patched version for your branch (see matrix above).
3) If you can’t patch immediately: disable zlib compression (workaround)
For EOL or high-risk upgrade windows, remove zlib from allowed compressors:
# mongod.conf
net:
compression:
compressors: snappy,zstd # remove 'zlib'Runtime equivalent guidance is also documented in public advisories.
4) Rotate secrets (do NOT skip)
Because this is a memory disclosure issue, assume anything in-memory may have been exposed:
Rotate MongoDB users/service account passwords
Rotate cloud keys/tokens used by the host/workload
Rotate app secrets/JWT keys stored in config stores
Review TLS private key exposure risk (environment-dependent)


Comments